Simple Cybersecurity Tips
- Keep Everything Updated:
- Regularly update your apps and devices to fix issues, address security concerns, and add new features.
- Updates make it harder for hackers to access your devices or accounts.
- Use Multi-Factor Authentication (MFA):
- Turn on MFA for an extra layer of security for both personal and organisational accounts.
- MFA requires more than one check, like a code from a text message and your passphrase, making it tough for cybercriminals to access your accounts.
- Backup Your Information:
- Set up regular backups to keep a digital copy of your important data.
- Backups can be stored on external devices or online servers (like the cloud), helping you restore your files if needed.
- Secure Passphrases:
- When MFA isn’t an option, use strong passphrases with four or more random words.
- Passphrases are hard for cybercriminals to guess but easy for you to remember.
- Recognise and Report Scams:
- Be cautious with emails, SMS, calls, and social media messages.
- Criminals may pretend to be someone you know; avoid clicking on attachments or links.
Level Up Your Cybersecurity by:
- Think Before You Post Online: Be mindful of the information you share.
- Sign Up for Alerts: Stay informed about new threats with our free alert service.
- Talk About Cybersecurity: Share tips with your family and friends.
- Avoid Public Wi-Fi for Banking: Use secure networks for online banking or shopping.
- Report Incidents: Help keep Australia secure by reporting cyber-attacks and incidents.
Report Cybersecurity Incidents:
- Visit cyber.gov.au
- Call 1300 CYBER1 (1300 292 371)
Explore additional resources at cyber.gov.au/learn. Stay safe online!
Setting up Multi-Factor Authentication for Microsoft 365 Accounts
Secure Your Account with Multi-Factor Authentication (MFA)
At HCI, safeguarding the security of our staff and the sensitive data we handle is our top priority. As part of our ongoing commitment to fortify our systems, we are excited to announce the implementation of Multi-Factor Authentication (MFA) for all Microsoft 365 accounts.
What is MFA?
Multi-Factor Authentication adds an extra layer of protection to your account by requiring a second form of verification alongside your password. This additional step enhances the security of your account and reduces the risk of unauthorised access.
How to Set Up MFA: Step-by-Step Guide
- Step 1: Sign in to Microsoft 365 Using your work or school account, log in to Microsoft 365 with your password as usual.
- Step 2: Choose Next After entering your password, click on “Next” when prompted for more information.
- Step 3: Set Up Microsoft Authenticator App We recommend using the free Microsoft Authenticator app as the authentication method. If you already have the app installed, select “Next” and follow the prompts to add your account. If not, download the app from the links provided:
- Google Android: Download from Google Play Store
- Apple IOS: Download from Google Play Store
- Step 4: Specify Your Additional Verification Method Follow the instructions to specify your additional verification method, which may involve linking the app to your account. After completing this step, the next time you sign in to Microsoft 365, you’ll be prompted to provide additional verification information or take action, such as entering the verification code from your authenticator app or received via text message.
- Note: You’ll likely only need the additional verification method the first time you sign in to a new app or device or after changing your password. In most cases, daily use won’t require the additional verification unless specified by our organisation.
Phishing Emails and Messages
Phishing emails are deceptive messages designed to extract sensitive information from you by posing as legitimate sources, including your bank, colleagues, or clients. Recognising the severity of this issue, we aim to raise awareness and prevent any potential scams.
An illustrative example of these phishing attempts is provided below:
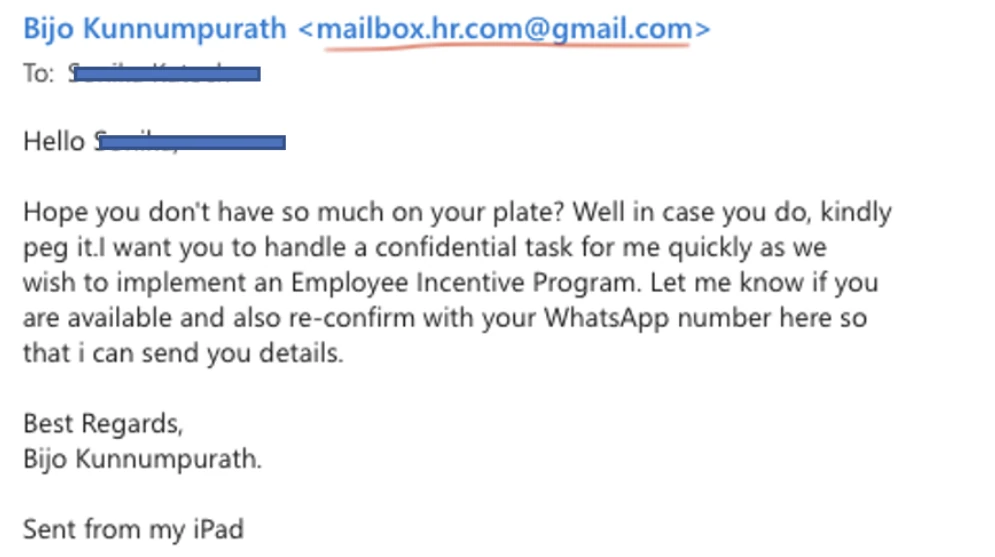
Emails received in Outlook on a computer
Emails received in Outlook on a mobile phone
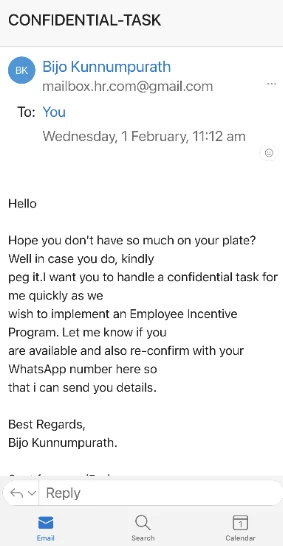
In these incidents, scammers request the sharing of a WhatsApp number and subsequently coerce individuals into purchasing gift cards (such as Apple or STEAM cards) and sharing the voucher codes. These actions are executed with a sense of urgency and confidentiality.
It is crucial to note that HCI staff or management will never request any payment from staff for workplace-related matters. Exercise extra caution when handling such emails, refrain from disclosing bank details or personal contacts, and safeguard your finances by avoiding these traps.
To fortify yourself and our organisation against phishing attacks, please adhere to the following guidelines:
- Avoid opening attachments or clicking on links in suspicious emails. These may contain viruses or spyware that can compromise your computer or steal your data.
- Do not reply to or forward suspicious emails. Report such emails to the IT department or student support team and promptly delete them.
- Carefully check the sender’s email address. Phishing emails often use spoofed or similar-looking addresses. Double-check the email ID, not just the Display Name. For instance, even if the sender’s name is listed as Dr. Bijo Kunnumpurath, the actual email ID may be different (e.g., mailbox.hr.com@gmail.com).
- Be vigilant for spelling and grammar errors, unusual or urgent requests, or offers that seem too good to be true. These are common indicators of phishing emails.
- If uncertain about an email’s legitimacy, verify with the sender through an alternate channel. Avoid using contact information provided in the email, as it may be fraudulent.
Advisory Regarding Atlassian Products
This advisory is crucial for Australian users of Atlassian products, including Confluence, Jira, and Bitbucket. Atlassian has recently released security patches addressing vulnerabilities in certain product versions. Here’s a summary of the key information:
Background / What has happened?
- Atlassian has released patches for security vulnerabilities, including critical ones (CVE-2023-22522, CVE-2023-22523, and CVE-2022-1471), impacting various versions of Confluence, Jira, and Bitbucket.
- The Australian Signal Directorate’s Australian Cyber Security Centre (ASD’s ACSC) emphasises the possibility of exploitation, given the historical significance of critical vulnerabilities in Confluence and Jira.
- Malicious cyber actors may employ patch differential analysis to reverse engineer vulnerabilities, making an exploitation campaign likely.
- Atlassian Cloud operated sites are not affected.
- An additional critical vulnerability has been addressed in the MacOS Atlassian Companion Application (CVE-2023-22524), requiring user interaction but still deemed critical.
Mitigation / How do I stay secure?
- If you operate Confluence, Jira, or Bitbucket, especially in internet-facing configurations, review the vendor advisories to determine if you are affected.
- Apply all vendor-recommended mitigations carefully if you are affected.
- Reassess the necessity of making your system internet-facing and consider filtering from the internet if possible.
Additional Information: For more details, refer to the following vendor advisories:
- https://confluence.atlassian.com/security/cve-2023-22522-rce-vulnerability-in-confluence-data-center-and-confluence-server-1319570362.html
- https://confluence.atlassian.com/security/cve-2022-1471-snakeyaml-library-rce-vulnerability-in-multiple-products-1296171009.html
- https://confluence.atlassian.com/security/cve-2023-22523-rce-vulnerability-in-assets-discovery-1319248914.html
- https://confluence.atlassian.com/security/cve-2023-22524-rce-vulnerability-in-atlassian-companion-app-for-macos-1319249492.html




